Are you aware of all the benefits of Microsoft 365 productivity tools? If not, don’t worry. You are not alone.
According to a report, most businesses use only 20% of all the features included in the latest version of Microsoft 365, formerly known as Office 365.
Microsoft Office 365 is an office suite of cloud-based solutions designed for all business sizes including small businesses, SMEs, and enterprises.
If you’re still using traditional on-premises infrastructure or considering a transition to a new software and productivity solution, it’s time to switch.
But what are all the benefits of Microsoft 365 and what makes it the better modern technology choice compared to its competitors?
In our blog post, we are going to discuss some compelling reasons why Microsoft Office 365 is the best cloud-powered productivity platform.
Before we discuss the benefits of Microsoft 365, let’s look at some of its cool features, which will help you in decision-making as per your business needs.
What are the Features of Microsoft 365?
Here are some of the latest features of Microsoft 365 that you must know:
1. Office Applications

Microsoft 365 is a bundle of cloud-based services, which gives you access to the latest versions of various productivity tools and office apps such as Microsoft Word, Excel, PowerPoint, Microsoft Teams, Outlook, Loop, and OneNote, all from a single platform.
Having all these tools in one place is essential for creating documents, spreadsheets, presentations, editing files with Office online, instant messaging and online meetings, managing email, and organising notes.
2. Storage and File Sharing
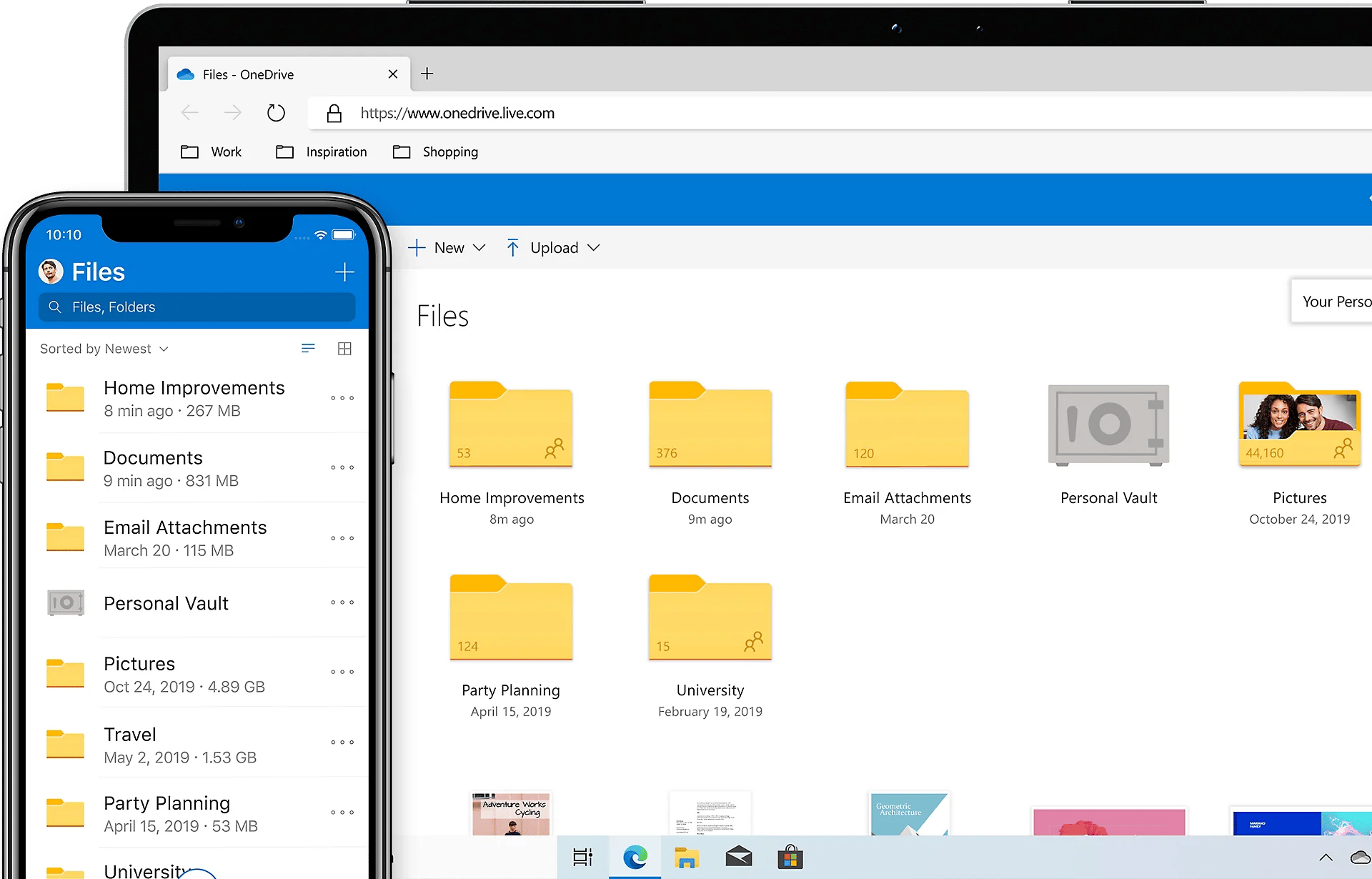
With OneDrive cloud storage for business, the user gets 1 TB of secure OneDrive storage where they can store, sync, and share files across devices.
OneDrive allows for easy collaboration on documents, enabling multiple users to work on the same files stored simultaneously, and offering the latest tools to manage user access (restrict access or remove users) and track changes in real-time.
3. Email and Calendar
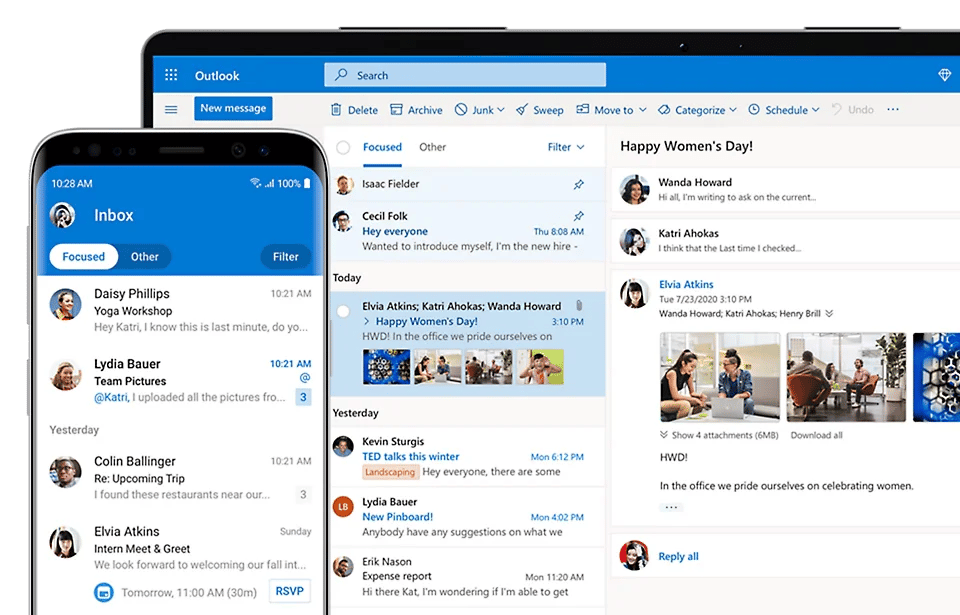
Microsoft 365 offers professional email hosting through Outlook, along with a calendar feature for managing appointments, online meetings, and events.
Outlook includes advanced email management tools, spam filtering, and integration with other Microsoft services.
4. Microsoft Teams
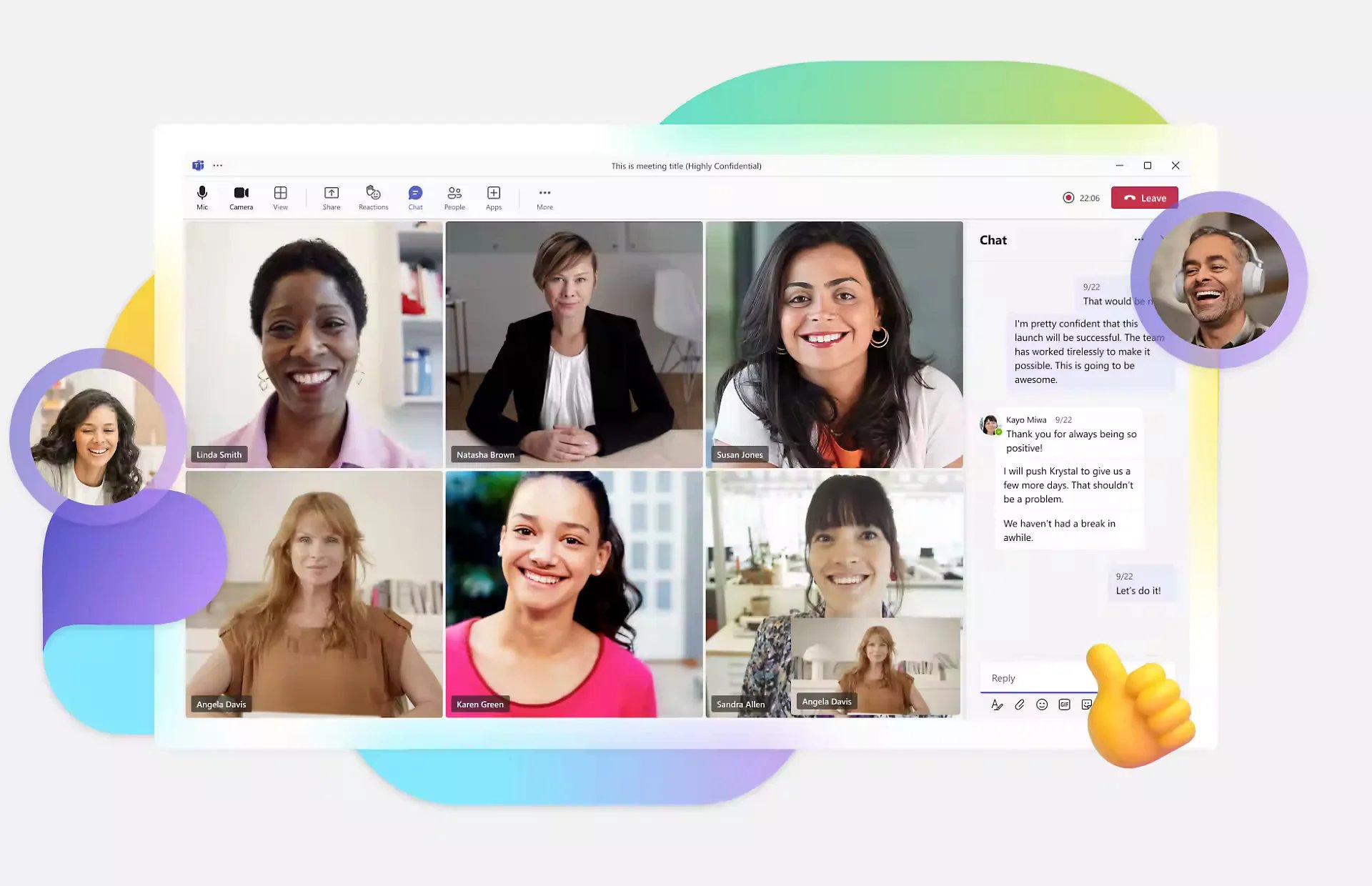
Microsoft Teams acts as a collaboration platform that combines all the tools which allow you to chat, do video calls, schedule meetings, can allow sharing documents within your teams and with multiple people across the business.
It provides a centralised hub for communication and collaboration, enabling teams to work together seamlessly regardless of their location.
5. Microsoft SharePoint and Exchange Online
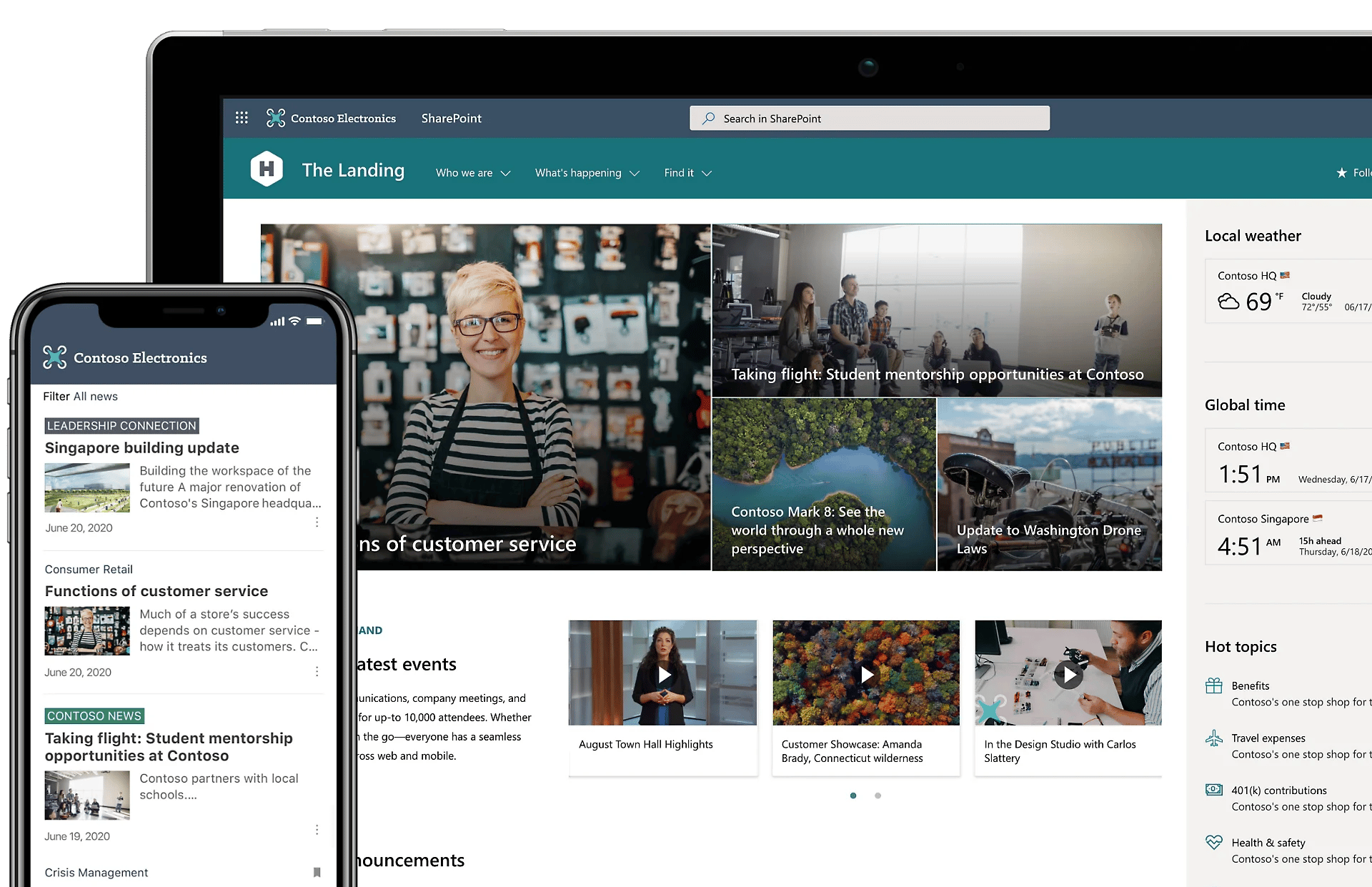
SharePoint Online is a web-based platform for creating intranet sites, document management, and collaboration.
It allows teams to share and manage content, build custom workflows, and create interactive dashboards to organise and access information efficiently.
6. Data Security
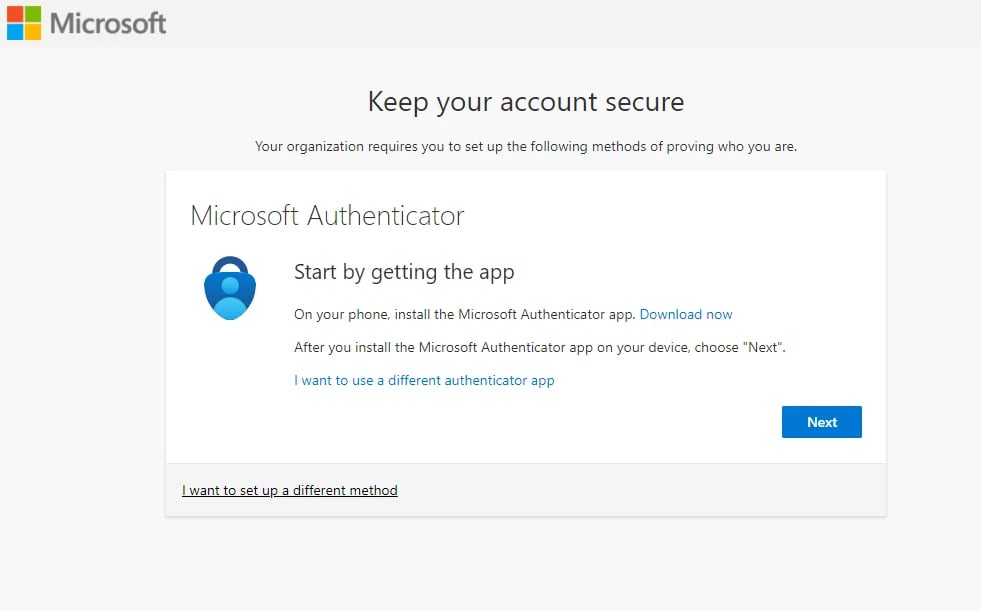
Microsoft 365 includes built-in robust security features like two-factor authentication to protect sensitive information and safeguard against cyber threats like malicious links.
This includes advanced threat protection, data encryption, identity and access management, mobile device management, and compliance tools to help businesses meet regulatory requirements.
For individuals, Microsoft Defender keeps your data secure with identity monitoring, risk alerts and expert guidance.
7. Business Intelligence
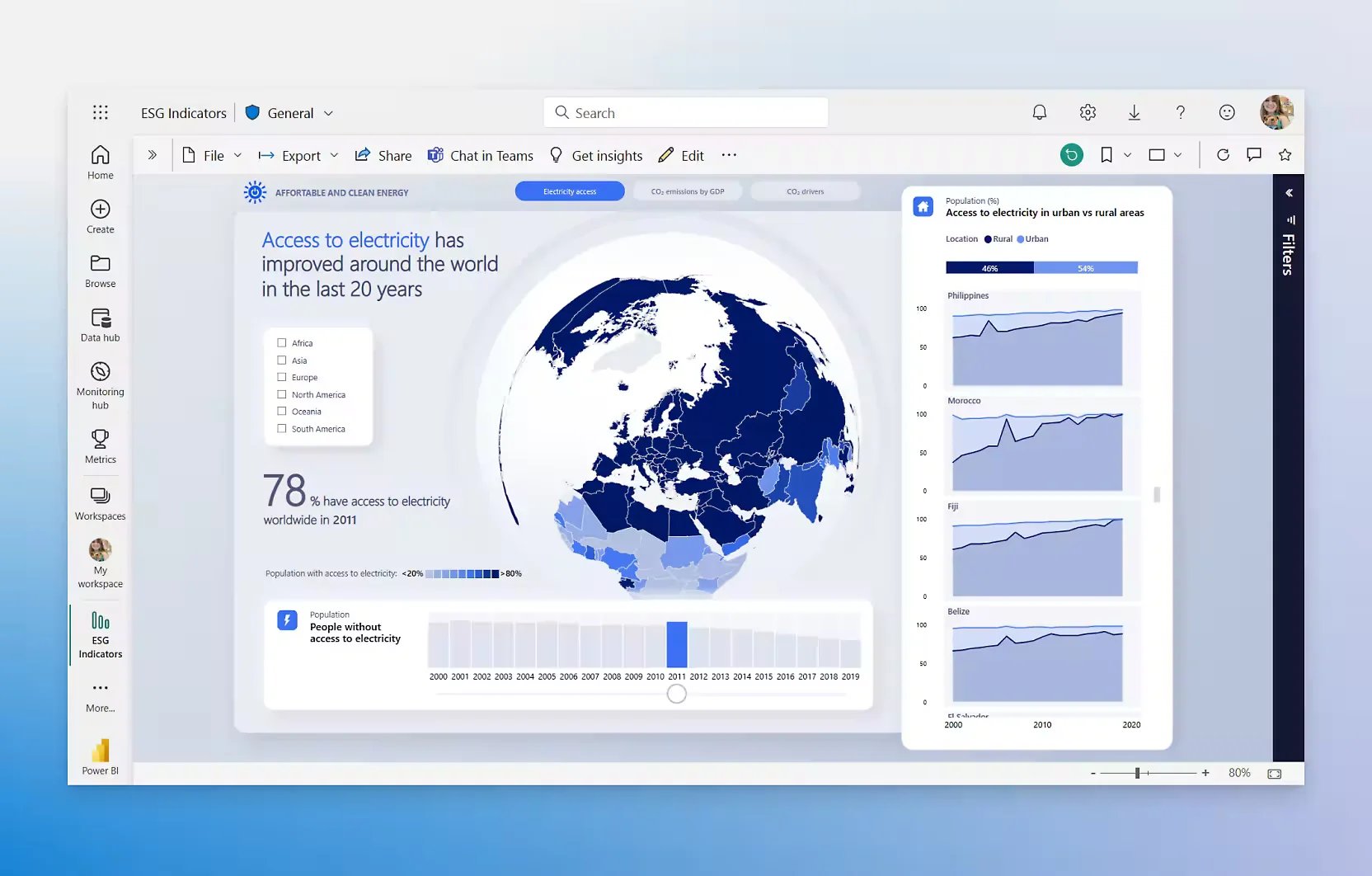
Microsoft 365 offers business intelligence tools such as Power BI for analysing data, creating interactive reports and dashboards, and gaining insights into business performance.
It integrates with other Microsoft services to provide a comprehensive solution for data visualisation and analytics.
8. Microsoft Forms
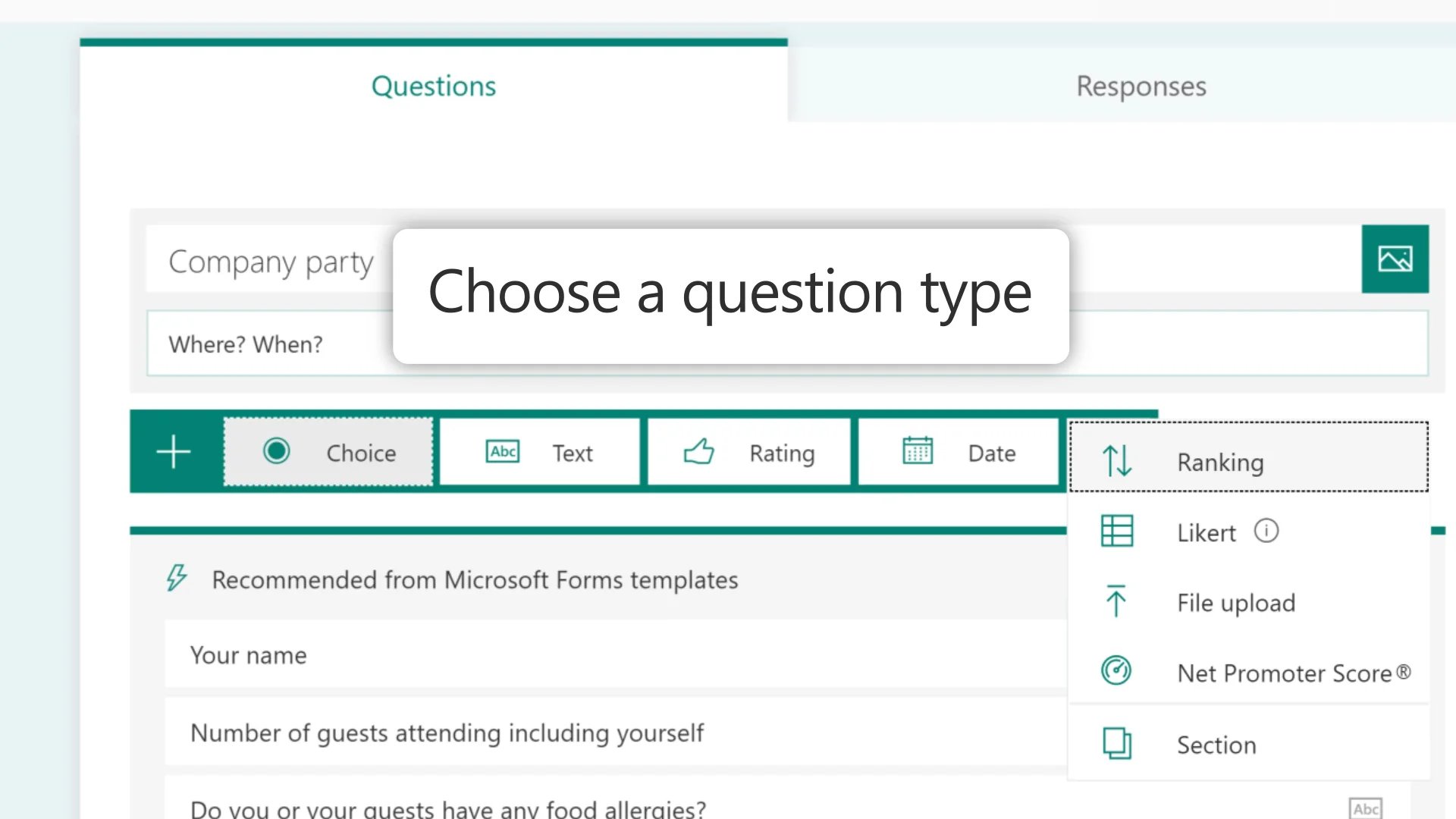
Microsoft 365 includes Forms which is a survey and data collection tool that allows users to create custom forms, quizzes, and polls to gather feedback, conduct surveys, and collect data from respondents. It provides built-in analytics to analyse responses and generate reports.
9. Microsoft Planner
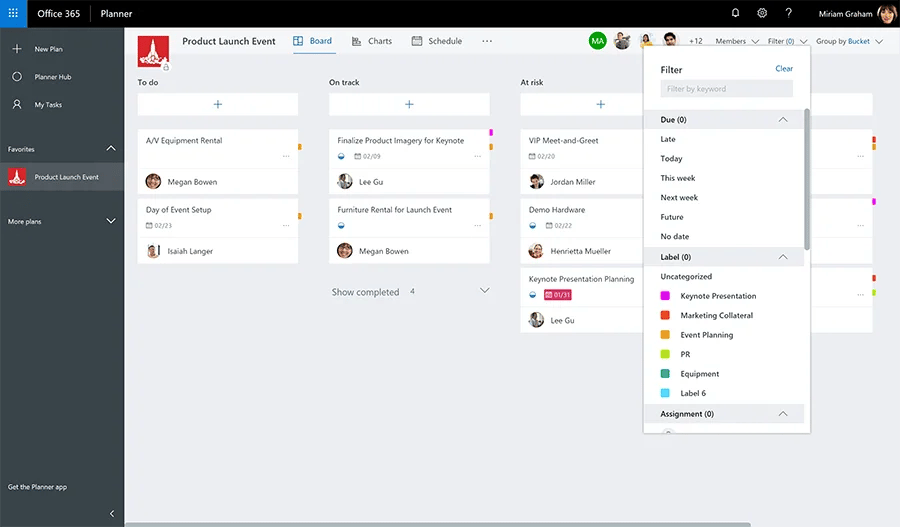
Planner is a task management tool that helps teams organise and track their work, assign tasks, set deadlines, and collaborate on projects.
It provides a visual overview of tasks and progress, making it easy to prioritise and manage workloads.
10. Yammer
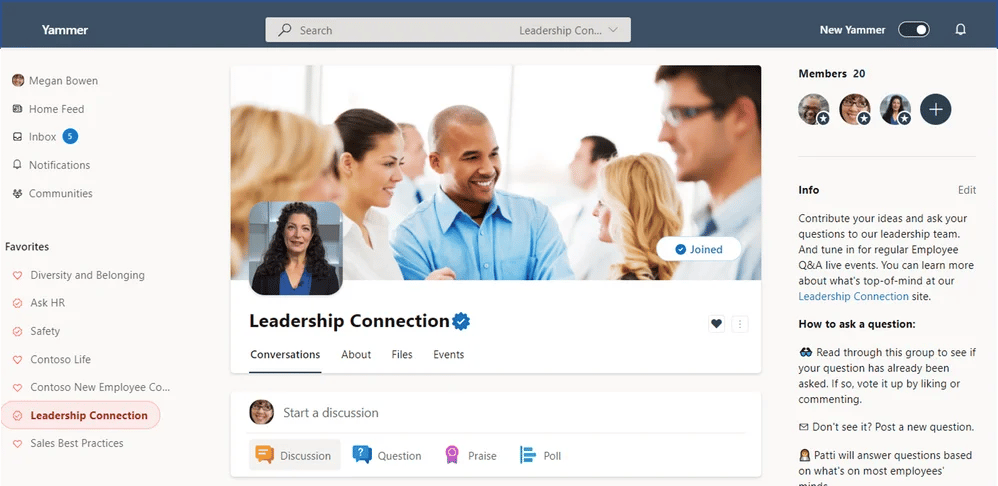
Yammer is a social networking platform designed for the enterprise, enabling employees to connect and collaborate across teams and departments. It provides a space for open communication, knowledge sharing, and community building within organisations.
11. Copilot for Microsoft 365
Microsoft Copilot for Microsoft 365 is an innovative AI tool that harnesses the power of large language models (LLMs), working hand in hand with your data stored within the Microsoft Graph and Microsoft 365 suite of applications.
By leveraging advanced language models and accessing data, Microsoft Copilot boosts your effectiveness within the Microsoft 365 ecosystem, serving as a powerful tool for users seeking to increase productivity.
12. Microsoft Loop
Microsoft Loop introduces a new productivity solution that unites teams, content, and tasks across different tools and devices.
It integrates a robust and adaptable canvas with portable elements that effortlessly transition and remain synchronised across applications. This enables teams to effectively collaborate, plan, and create together.
Now, let’s dig deeper into the benefits of Microsoft 365.
What are the benefits of Microsoft 365?
Here are 8 reasons why you should switch to Microsoft 365 for your business:
1. Accessibility and Collaboration
One of the most significant benefits of Microsoft 365 is its accessibility. As a cloud-based software, you can access to co-authoring documents, edit documents, emails, and software applications from anywhere and anytime with the Office suite for mobile apps.
All you need is an internet connection. This flexibility is particularly beneficial if you need to collaborate with your remote employees, all you need is authorised access to your workspace. They can access everything they need, regardless of your employees’ mobile devices.
Office 365 comes with various collaboration tools, such as Exchange Online, SharePoint, OneDrive, and Teams, making it easy for other team members to collaborate on projects, share information, and communicate in real time.
The co-authoring feature allows multiple users to work on the same document simultaneously, making it easier to collaborate on projects without worrying about version control.
2. Scalability and Flexibility
With Office 365, you can easily scale your business by adding or removing users as needed. The subscription-based pricing model allows you to choose the right solution that meets your specific needs and budget.
As your business grows, you can easily upgrade to a more comprehensive plan without incurring any additional expenses for hardware or software installation.
Additionally, Office 365 offers various plans tailored to meet the needs of businesses of all sizes, from small businesses to large enterprises.
You can mix and match different plans to suit the individual requirements of various departments or teams within your organisation, ensuring everyone has access to the right tools and resources.
3. Data Security and Compliance
Microsoft 365 uses robust security measures like advanced encryption techniques, data loss prevention, threat detection and multi-factor authentication to prevent unauthorised access to your data.
Moreover, the platform is continuously monitored for any potential threats, and Microsoft deploys regular updates to address any vulnerabilities.
Microsoft also ensures that your data is stored in compliance with various industry regulations and standards, such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Family Educational Rights and Privacy Act (FERPA).
Regular audits and certifications help maintain transparency and customer satisfaction.
4. Automatic Updates and Maintenance
Microsoft 365 eliminates the need for manual software updates and maintenance. As a cloud-based platform, all the latest version updates, patches, and new features are automatically rolled out without any intervention from the user.
This means you can always get automatic upgrades and access the most up-to-date software without worrying about compatibility issues or downtime during updates just by having a good internet connection.
The automatic update feature also translates to cost savings, as you no longer need to invest in IT staff to manage software updates and maintenance.
5. Integration with Other Microsoft Products and Services
One of the key benefits of Microsoft Office 365 is its seamless integration with other Microsoft products and services.
Whether you’re using Power BI for data analysis, Dynamics 365 for customer relationship management, or Azure for cloud computing, Office 365 can easily integrate with these services, providing a unified and cohesive experience for users.
This integration not only improves productivity but also simplifies the management of various services, as you can manage everything from a single dashboard.
6. Cloud Storage with 1 TB of OneDrive storage
Another big advantage of Microsoft 365 is data storage through OneDrive, which allows you to store and access files securely from anywhere.
This eliminates the need to rely solely on local storage solutions and ensures that documents are always up-to-date just by having a secured internet connection.
7. Subscription-based model for Cost-Effectiveness
The next key benefit of Microsoft 365 is its subscription-based service model, which can be more cost-effective for businesses compared to purchasing individual software licenses.
Microsoft 365 can help you by providing access to all tools and services at a single subscription plan. You can choose the subscription plan that best fits your business needs and budget from the range of Microsoft 365 plans.
Furthermore, the cloud-based nature of Microsoft 365 means there’s no need for expensive on-premises infrastructure, reducing overall IT costs.
Plus, with the ability to scale your subscription up or down as your business grows or changes, you’ll only ever pay for what you need for all the apps.
8. Copilot for Microsoft 365 for enhanced productivity
One of the key advantages of Microsoft 365 is the addition of Copilot, a productivity tool that can enhance your employees’ productivity at no extra cost.
Copilot is readily available for use in Microsoft Word, Excel, PowerPoint, Microsoft Teams, Outlook, Microsoft Loop, Microsoft Edge and Copilot formerly Bing Chat Enterprise all of which are included in your Microsoft 365 package.
Moreover, Copilot boasts advanced security features that ensure optimal data loss prevention. You can rest assured that Microsoft does not track any of your business data.
Is Microsoft 365 worth paying for?
Yes absolutely, Microsoft is worth paying for several reasons such as you can get the latest features and security updates, collaborate with teams anywhere and increase productivity and flexibility for your business.
The subscription model of Microsoft 365 provides you with regular updates and ensures you access to the updated features and security patches.
Additionally, with the cloud-based services of Microsoft 365, you can seamlessly collaborate and enhance employee experience by working remotely, which increases productivity and flexibility.
Ultimately, for many businesses, the convenience, reliability, and full suite of tools offered by Microsoft 365 can justify the investment.
Why should I switch to Microsoft 365?
Making the switch to Microsoft 365 can have a significant positive impact on your organisation’s productivity, seamless collaboration, and overall efficiency.
With its cloud-based accessibility, productivity tools, device security policies, advanced security features, regular updates, advanced threat analytics, and cost savings subscription model, Microsoft 365 is the ideal solution for modern work businesses looking to stay competitive in today’s fast-paced digital landscape.
Don’t miss out on the opportunity to empower your employee experience and streamline your business operations – subscribe to Microsoft Office 365 today.
How Can Castle Help Your Business?
Are you searching for the best Microsoft product consultants for your business? At Castle Computers, we offer premium cloud transformation services and technical support tailored to your business needs.
We comprehend the requirements of businesses and device-all-encompassing solutions to ensure your technology remains secure, up-to-date, and advantageous, giving you a competitive edge.
Contact us today and let us assist you in achieving success with these benefits of Microsoft 365.